I was asked by a customer to filter trafic on WIFI network. So I used the ability to use attributes returned by radius server to apply filtering rules on IAP cluster.
Some technical information about the installation :
- AP 303 in instant controller mode in version 8.3.0.3
- Radius server is NPS role on Windows server
- Windows server with Active Directory
- Airwave in version 8.2
Nothing new regarding initial installation and configuration for NPS role on windows server.
Below, the scheme validated by customer to authentify their users.

This client has a mix of domain computer and BYOD device (android and apple phone, personnal computer).
Rules were defined as follows :
- Customer’s computer in domain should be authentified directly without user authentication
- Others equipments can be authentified using users authentication depending on the security group affected to the user
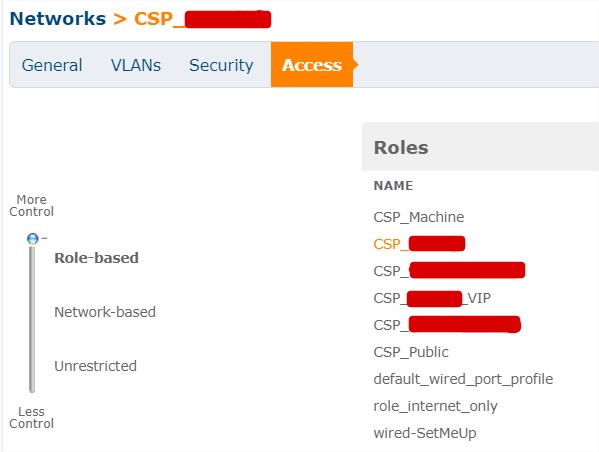
To do that, I used the ability to match special string returned by NPS server with role created on IAP controler. Then, I create filtering rule based on created role. In short, radius attribute = role.
As you can see above, default role is the name of the SSID, then a role is applied depending off string (Callback_number attribute) received from radius. Multiples roles are configured to filter several networks.
In details for a WIFI supplicant that is a computer in AD domain:
- WIFI client start EAP connexion to AP
- AP forward identity to radius
- NPS verify that the computer is from the group Computer in domain
- NPS grant or refuse the access and return special string to the IAP controler
- IAP controler apply filtering rule according to the string returned
In details for a WIFI supplicant with computer not in AD domain but with a user account member of special security group in AD:
- WIFI client start EAP connexion to AP
- AP forward identity to radius
- NPS verify that the computer is from the group Computer in domain
- NPS pass this rule because computer is not in domain. Next rule is matched (security group match)
- NPS grant or refuse the access and return special string to the IAP controler
- IAP controler apply filtering rule according to the string returned